As systems to control energy-using manufacturing equipment become more connected to the internet, it is important for plant operations staff to have an understanding of cybersecurity risks and to coordinate risk management activities within their organization.
Small businesses may not consider themselves targets for cyber-attacks. However, they have valuable information cyber criminals seek, such as employee and customer records, bank account information, and access to larger networks. They can be at a higher risk for cybersecurity attack because they have fewer resources dedicated to cybersecurity.
By addressing risk areas, you can protect your business from damage to information or systems, intellectual property theft, regulatory fines/penalties, decreased productivity, or a loss of trust with customers.

IAC Cybersecurity Assessments
Industrial Assessment Centers work with manufacturing clients to increase awareness of cybersecurity risks and potential mitigation activities. As part of facility site visits, IAC clients may elect to receive cybersecurity risk assessments to identify security and privacy deficiencies to the business infrastructure, with a focus on vulnerabilities associated with industrial controls systems.
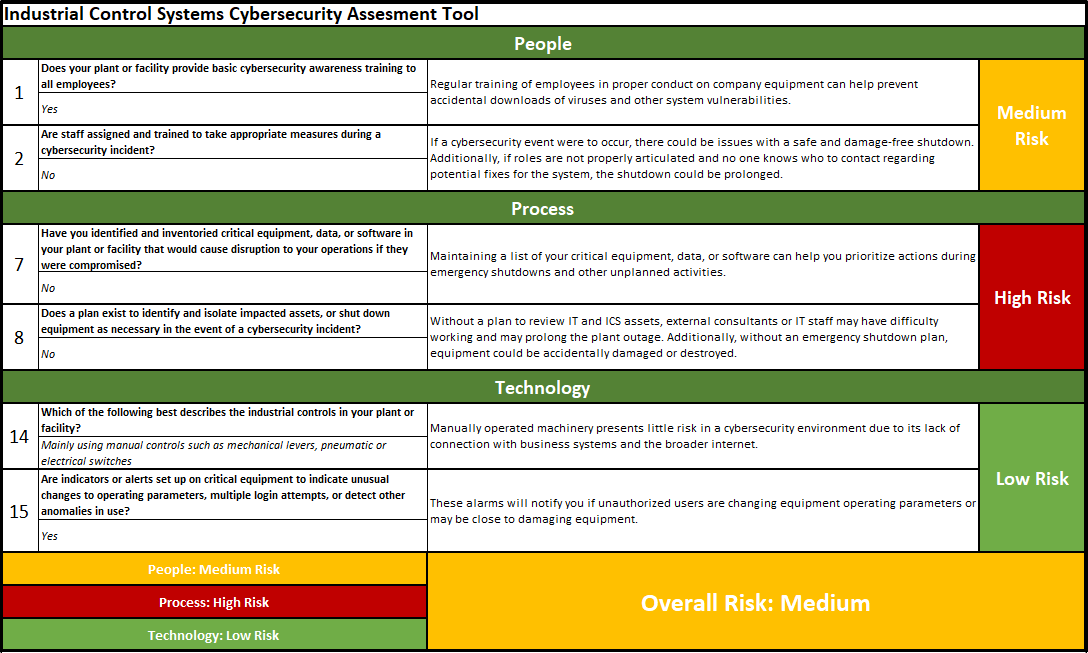
The IAC Industrial Control Systems Cybersecurity Assessment Tool includes 20 simple questions to characterize industrial controls systems and plant operations. The tool then provides a high level assessment of risk (high, medium, or low). The companion User Guide provides additional context for the questions included in the tool, to help clients understand how certain business practices lead to cybersecurity risk. Upon conclusion of the assessment, the tool generates a customized list of action items associated with the risks identified. For additional guidance, IACs refer clients to additional technical resource materials available through the NIST Manufacturing Extension Partnership (MEP) and other organizations.
IAC Industrial Control Systems Cybersecurity Assessment Tool
Download Asssessment Tool Download User GuideCybersecurity Fundamentals for Small and Medium Sized Manufacturers
Most plant operations managers are not cybersecurity experts, but can benefit from a basic understanding of cybersecurity risks and mitigation activities. A guidance document provided by NIST, NIST Small Business Information Security: The Fundamentals, provides a thorough and easily readable overview of cybersecurity basics.
As a first step, organizations need to understand their cybersecurity risks, to determine where the organization is vulnerable and may be subject to disruption of systems and processes. Organizations can use helpful checklists from the NIST document, or other cybersecurity assessment tools, to conduct the following activities:
- Identify what information your business stores and uses
- Determine the value of your information
- Develop an inventory of technologies used to store and process information
- Understand your threats and vulnerabilities
Once risks are understood, organizations can determine appropriate mitigation activities. Example activities are shown below, grouped into the five broad categories of the NIST Cybersecurity Framework:
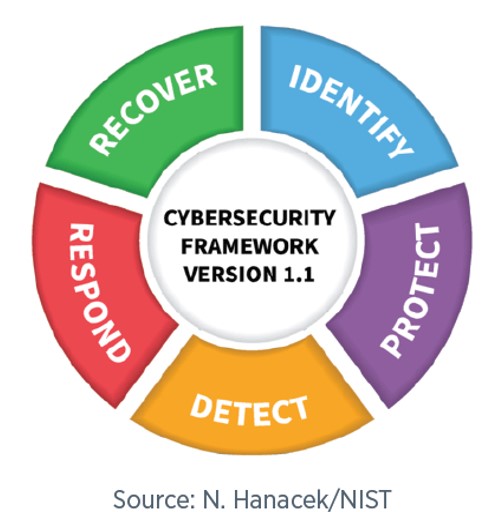
IDENTIFY
Identify and control who has access to your business informationConduct background checks
Require individual user accounts for each employee
Create policies and procedures for information security
PROTECT
Limit employee access to data and informationInstall surge protectors and uninterruptible power supplies (UPS)
Patch your operating systems and applications
Install and activate software and hardware firewalls on all your business networks
Secure your wireless access point and networks
Set up web and email filters
Use encryption for sensitive business information
Dispose of old computers and media safely
Train your employees
DETECT
Install and update anti-virus, -spyware, and other –malware programsMaintain and monitor logs
RESPOND
Develop a plan for disasters and information security incidentsRECOVER
Make full backups of important business data/informationMake incremental backups of important business data/information
Consider cyber insurance
Make improvements to processes/procedures/technologies
Additional Cybersecurity Assessment Tools
Once an organization has a basic understanding of cybersecurity risks and vulnerabilities, a more detailed assessment can be used to determine mitigation actions and security controls. Some of the common tools used to perform assessments are listed below. The CSET tool is one of the more comprehensive tools available for small and medium-sized manufacturers. Organizations can explore resources available to help conduct assessments (e.g., IACs, MEPs, third party vendors).
- Cyber Security Evaluation Tool (CSET): Comprehensive desktop software tool that guides users through a step-by-step process to assess their control system and information technology network security practices against recognized industry standards.
- NIST MEP Cybersecurity Assessment Tool: Online easy-to-use checklist that provides an assessment of business systems.
- Department of Energy C2M2 Model: Model used to measure the maturity of an organization’s cybersecurity capabilities, developed by energy sector subject matter experts.
- Department of Homeland Security Cyber Resilience Review: No-cost, non-technical assessment to evaluate an organization’s operational resilience and cybersecurity practices.
Additional Resources
Provides cybersecurity resources for small manufacturers, based on the NIST Cybersecurity Framework
Interactive Infographic: How Secure is Your Factory Floor?
NIST Small Business Information Security: The Fundamentals
NIST MEP Cybersecurity Assessment Tool
NIST Resources on DFARS Cybersecurity Requirement for suppliers to DOD
Provides resources focused on industrial controls systems
Overview of Cyber Vulnerabilities of ICS
Recommended Practices technical resources to mitigate vulnerabilities of controls systems
Cyber Threat Source Descriptions
Critical Manufacturing Sector Cybersecurity Framework Implementation Guidance
ICS-CERT Annual Assessment Report summary of Top Vulnerabilities